Windows Server 2025 (26080) – ADPrep error 0x800b010a
There is always something new we can learn by doing things we haven’t done before. And sometimes this will bring back old memories…
Recently I started testing latest preview of Windows Server 2025 (build 26080) and I managed to stumble upon on old (looks like still relevant) problem, that I had to deal with years ago.
Before introducing new version of Windows Server as a Domain Controller (DC) (this is not required when new server becomes member server and not a domain controller) into existing environment, it’s recommended to prepare that environment with the execution of ADPrep tool (found in .\support\adprep folder on the installation media that matches the version of the server we are adding as new domain controller). As mentioned, it’s recommended and not required – if admin account doing the promotion of new server to a DC role has sufficient privileges (usually membership in Schema Admins and Enterprise Admins is sufficient), this can be done automatically (forestprep and domainprep) just by using Server Manager and adding required role with the build-in wizard:

The same would also apply when using PowerShell to promote existing member server to a DC (if admin account doing the promotion has sufficient privileges, forestprep and domainprep is automatically executed when/if needed) :
Install-WindowsFeature -name AD-Domain-Services -IncludeManagementTools
Test-ADDSForestInstallation -DomainName corp.contoso.com -InstallDns
Install-ADDSForest -DomainName corp.contoso.com -InstallDNS
Before upgrading one of the existing domain controllers (when doing in-place upgrade to a new version of Windows Server), it’s mandatory to run the ADPrep tool. Per documentation:
– For an in-place upgrade of an existing DC, you must run adprep /forestprep and adprep /domainprep manually.
– You need to run Adprep /forestprep only once in the forest for each newer version of Windows Server.
– Run Adprep /domainprep once in each domain in which you have DCs that you’re upgrading for each newer version of Windows Server.
When I tried to run adprep /forestprep on one of my existing domain controllers, I got stopped with an interesting error: Failed to verify file signature: error 0x800b010a.

As it happens, I’ve seen this error years ago and the solution still works…
The problem is with the digital signature on the schupgrade.cat file next to adprep.exe tool. The root certificate used to sign this file is not trusted and because of that ADPrep fails to do its thing.

Solution is simple – just check the digital signature of the file and install the root cert into local “Trusted Root Certification Authorities” store. After that is done, ADPrep should work as expected:


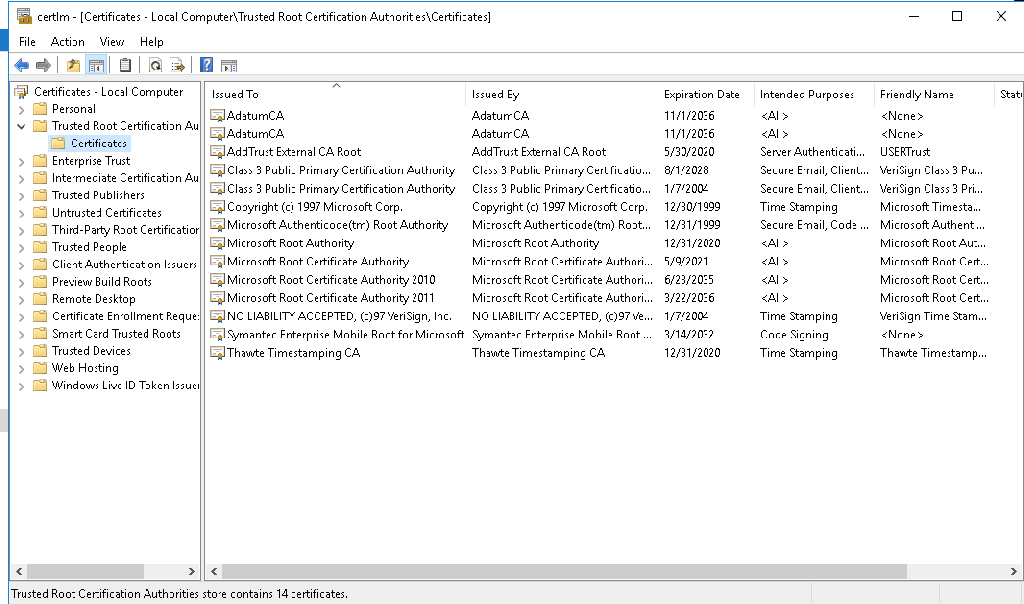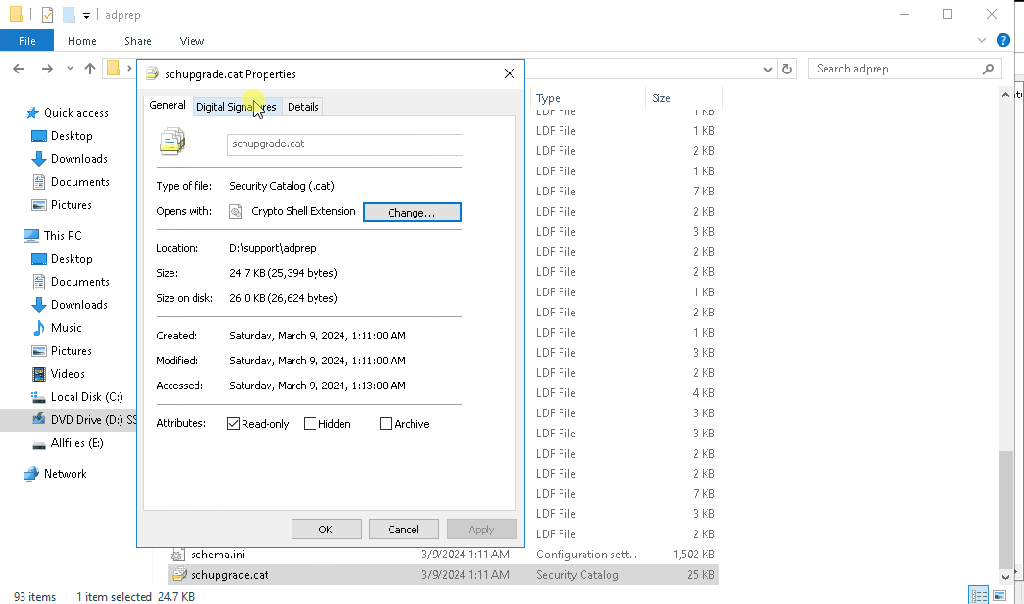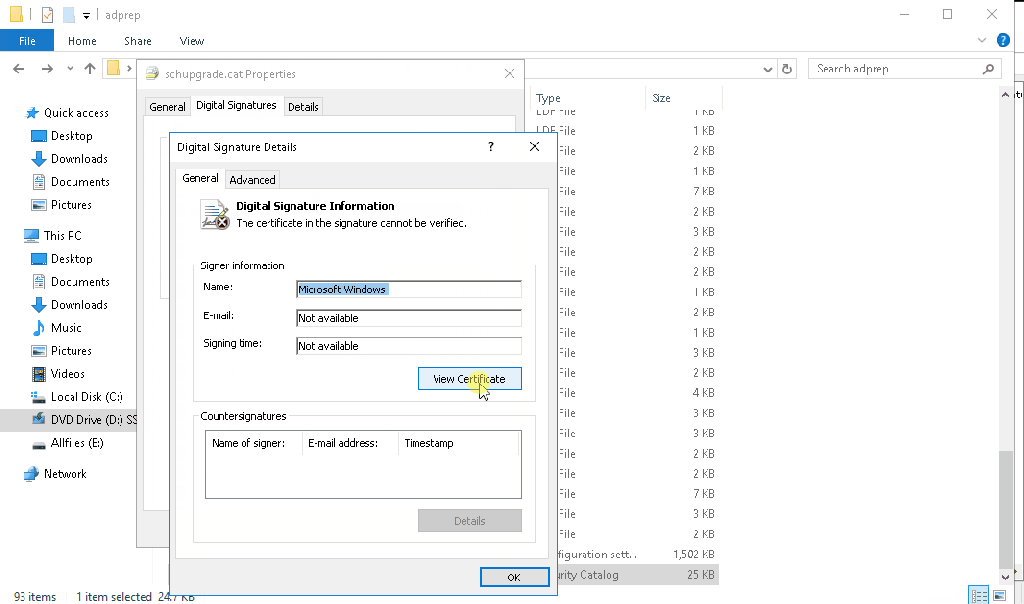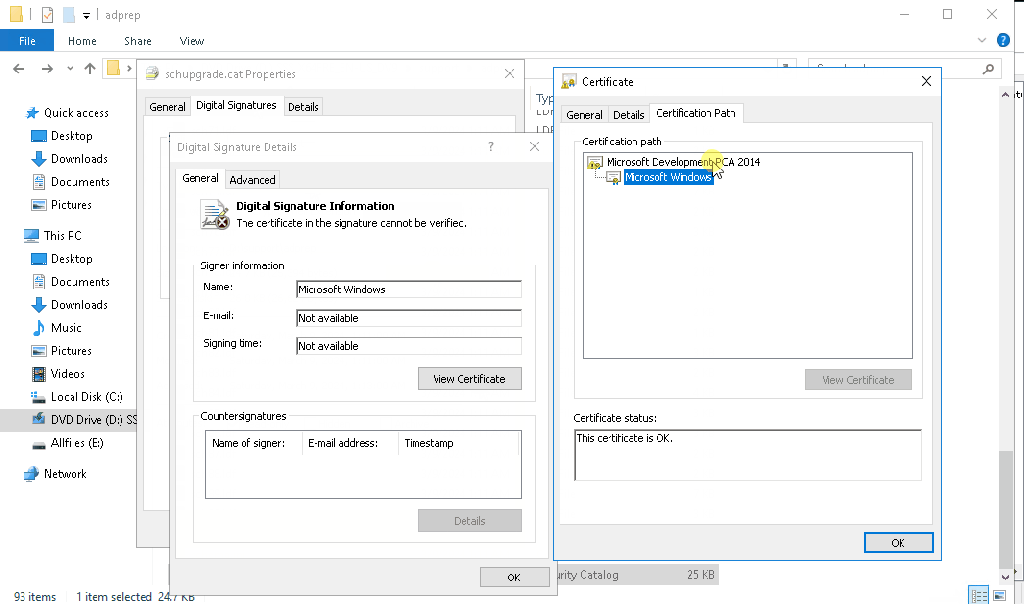
It might happen that you don’t see the “Microsoft Development Root Certificate Authority 2014” certificate in the certificate path (for me this happened on server 2016 DC, that was at the time not connected to the internet):
If that happens to you too, you can save below string as CER file and import it as usual:
-----BEGIN CERTIFICATE-----
MIIGBTCCA+2gAwIBAgIQB48KnQPfEZ5DTk/sG/AjWjANBgkqhkiG9w0BAQsFADCB
lDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1Jl
ZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjE+MDwGA1UEAxM1
TWljcm9zb2Z0IERldmVsb3BtZW50IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5
IDIwMTQwHhcNMTQwNTI4MTY0MzQ2WhcNMzkwNTI4MTY1MTQ4WjCBlDELMAkGA1UE
BhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAc
BgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjE+MDwGA1UEAxM1TWljcm9zb2Z0
IERldmVsb3BtZW50IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTQwggIi
MA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDCD39tSbs58E2UP+j7TcXrO+Eo
WrmJKkZ+pcMzJx2CiT/rM6GHaurogrnaw5130TXAy4M2cqZXGRK8FeLIPHuDYjQU
1au23jaLoVpxplGWpwYzsyIdFGJTwqWvmkDKvixIVJnnKpNop2kZC5lpO8GyrK6U
3F+rfgLK3jyndKaMEKDlrracNe+DixDllyq6kWuaakWV2dBUcY5lP8SKU8oeOEcK
6dBBhKXaHmYBZQTmUFt3NfW0LikyDMa/X2HuMiC3fDn5Efr/YF7+xmn0bx4d7R0G
52UemhEuY0QGXzFDFzPpoyaC1EuDEk/SoSYDJUjhOr2E9YrVtG4a6HEgDkVTAWet
4x5r6LLkq/31O466Z69ZhMxcddCdqlxyxCY2oqwyTGqx+DMXRNKnfXDu63CUmrzq
uhwQS2NbON3SJUUEsvCzWnwLCo4hQGQ3EU2WaUUz5JODnvmztRwrBXHqbcznSLa2
3oBQEMpJOLNZBXBOvZ6IAiJYZInrQNqxLS1qQIhdI8M+0PXVt5CKKFQ5YqLFxrG/
dM2GlflFa8zyB+qsXNM296J6tbRyUyoGPsM3lFhYsUpxu1zNnLKvEJrZQzY+UoUZ
50IokRGMjOe73+bIVQhzdfOWDYa30uUGssCKVKhhdyB9bNH+umjzRUqvEYTrhn0v
BPNU6iD/1ds9JQJwhwIDAQABo1EwTzALBgNVHQ8EBAMCAYYwDwYDVR0TAQH/BAUw
AwEB/zAdBgNVHQ4EFgQUhXAAn3dZHoysPJ93JigZzJrBjzIwEAYJKwYBBAGCNxUB
BAMCAQAwDQYJKoZIhvcNAQELBQADggIBAE8ldL0fYk9fD/dCItfR1lMEIy7F1dcH
K2t5O19tkO0TVdOC8fUCjz75liZ+DUIYdvxgVYJahr0RMzlpD87gsCvxXRnf2NL6
hqTMzazw0K6aiyskjwPBNQ0gs9/HQup3KS4KEvwLGkWN2TGEDY0CwKz60hK/Hmo0
PuqDAKNIdU5yZi2hpRKfN6hdSndZz9Y6/DDFpgmlv7EI4/ssn3bE+05hHW0j83Zp
hetJuw33PdCqBbzdPW6ARF7ZmmjsyYnH5hoY+GCg54z25lFvDuAluGP5+cILjDyc
svBCzb7D9f5JKVWcXoaW+6HtbSaG6Lggi1zG5y0xxarKfUt9oFmkHvtQcemvz9aq
DZnejpUmlzGl9H9t9GgVuOP3rdjv0Th1Al/9bU78tvwvRRupytEeev91GBU2wSDk
X0g6let75PX29P7JSyGiqeqKmSXL6ERAkNU5tGsjm1K8wMF+F2ZuZQv1dBWWqGbt
hWhUsiTodYhkRYmFPHpla5bg8lnqRyVmD2obDD/USuZLJhdHCf7U17jgzucvlK2A
i2dwzLd7zxsrudFbvbgDXLHwG0Es5lNVFudKDkEImTfiqddtDmpF5ezjiKn9tpvD
KCDOq8KTa1FlU7+gXnudJjSaUUyMpjjVhls8Ve5Q7AALyqzcyhCr3xib0qwMjQhF
Fa+FNTVa5Sa8
-----END CERTIFICATE-----
Above certificate is base-64 encoded CER file for the “Microsoft Development Root Certificate Authority 2014”.