Archive
Windows Server 2025 (26080) – ADPrep error 0x800b010a
There is always something new we can learn by doing things we haven’t done before. And sometimes this will bring back old memories…
Recently I started testing latest preview of Windows Server 2025 (build 26080) and I managed to stumble upon on old (looks like still relevant) problem, that I had to deal with years ago.
Before introducing new version of Windows Server as a Domain Controller (DC) (this is not required when new server becomes member server and not a domain controller) into existing environment, it’s recommended to prepare that environment with the execution of ADPrep tool (found in .\support\adprep folder on the installation media that matches the version of the server we are adding as new domain controller). As mentioned, it’s recommended and not required – if admin account doing the promotion of new server to a DC role has sufficient privileges (usually membership in Schema Admins and Enterprise Admins is sufficient), this can be done automatically (forestprep and domainprep) just by using Server Manager and adding required role with the build-in wizard:

The same would also apply when using PowerShell to promote existing member server to a DC (if admin account doing the promotion has sufficient privileges, forestprep and domainprep is automatically executed when/if needed) :
Install-WindowsFeature -name AD-Domain-Services -IncludeManagementTools
Test-ADDSForestInstallation -DomainName corp.contoso.com -InstallDns
Install-ADDSForest -DomainName corp.contoso.com -InstallDNS
Before upgrading one of the existing domain controllers (when doing in-place upgrade to a new version of Windows Server), it’s mandatory to run the ADPrep tool. Per documentation:
– For an in-place upgrade of an existing DC, you must run adprep /forestprep and adprep /domainprep manually.
– You need to run Adprep /forestprep only once in the forest for each newer version of Windows Server.
– Run Adprep /domainprep once in each domain in which you have DCs that you’re upgrading for each newer version of Windows Server.
When I tried to run adprep /forestprep on one of my existing domain controllers, I got stopped with an interesting error: Failed to verify file signature: error 0x800b010a.

As it happens, I’ve seen this error years ago and the solution still works…
The problem is with the digital signature on the schupgrade.cat file next to adprep.exe tool. The root certificate used to sign this file is not trusted and because of that ADPrep fails to do its thing.

Solution is simple – just check the digital signature of the file and install the root cert into local “Trusted Root Certification Authorities” store. After that is done, ADPrep should work as expected:


It might happen that you don’t see the “Microsoft Development Root Certificate Authority 2014” certificate in the certificate path (for me this happened on server 2016 DC, that was at the time not connected to the internet):
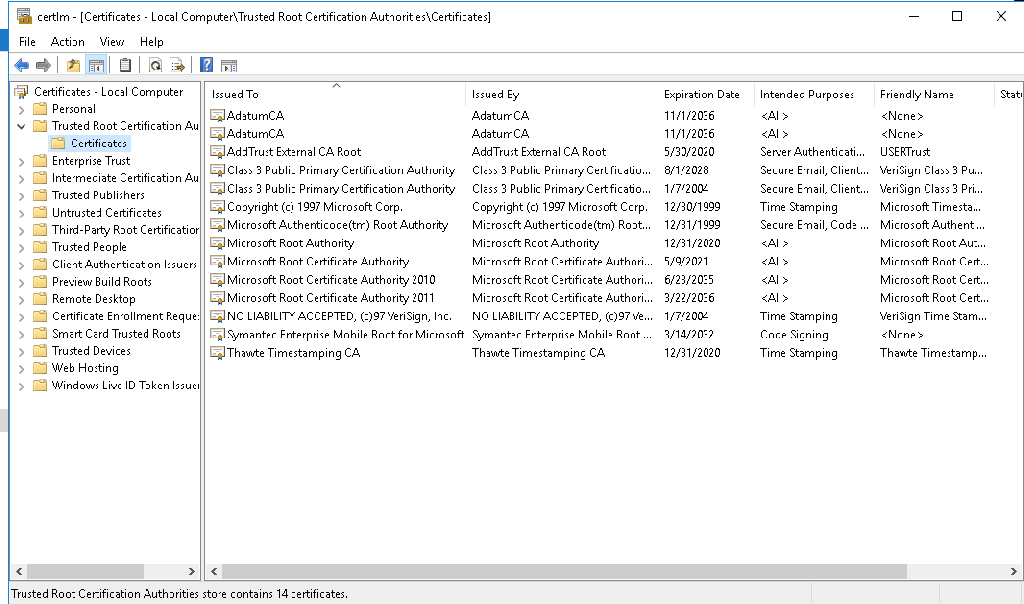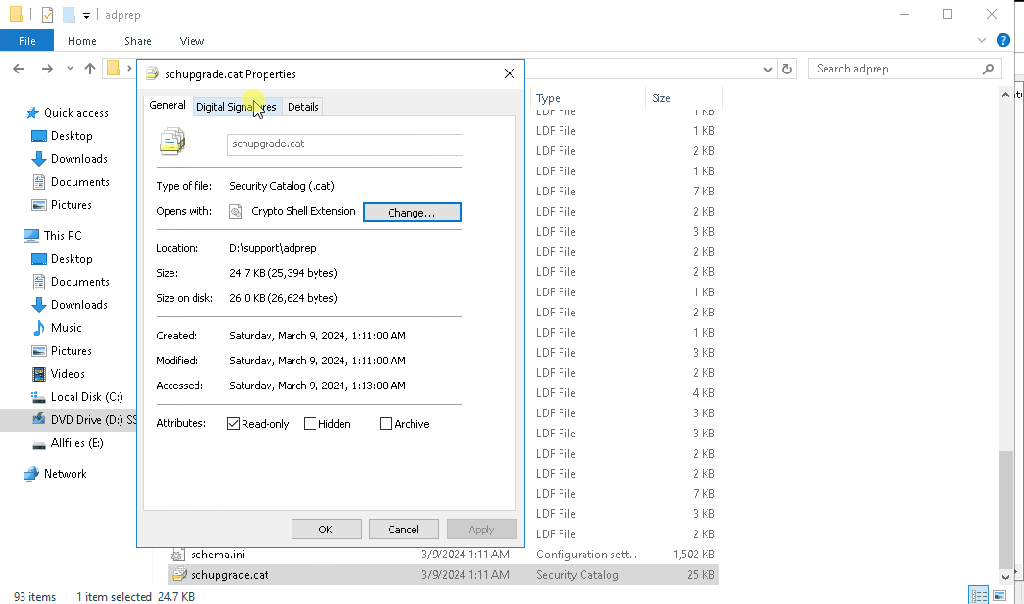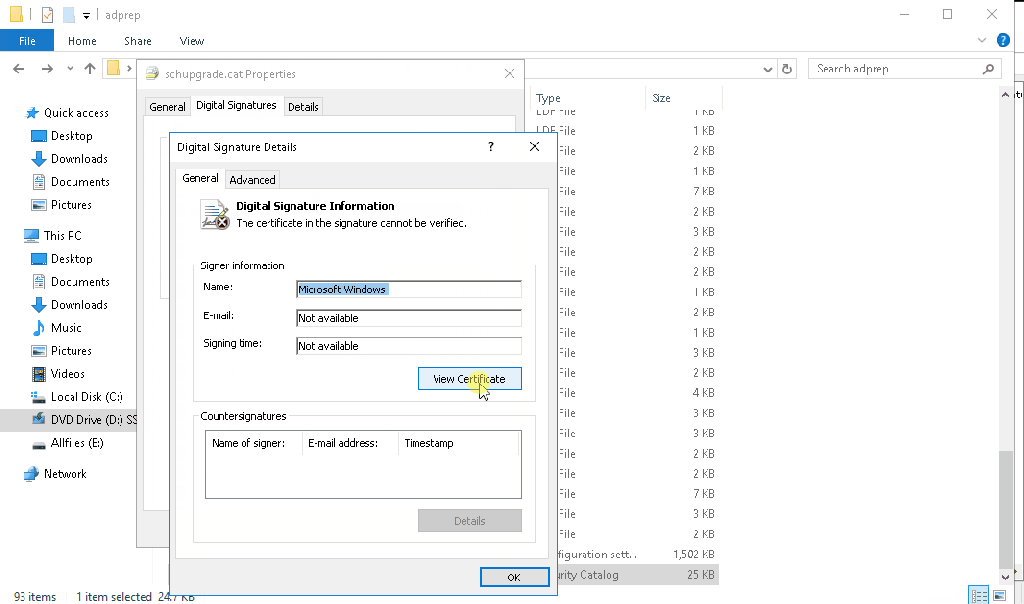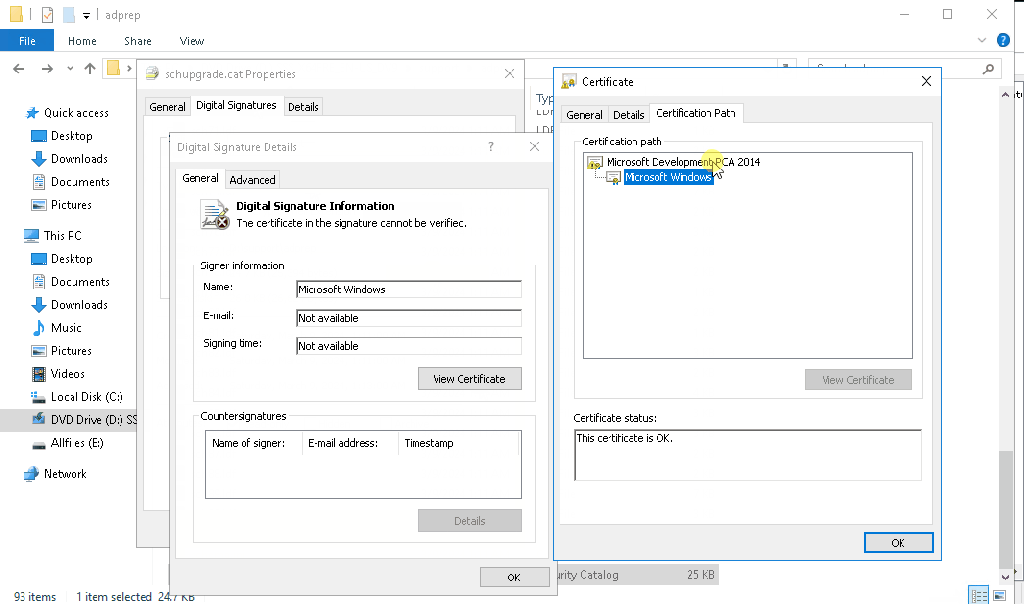
If that happens to you too, you can save below string as CER file and import it as usual:
-----BEGIN CERTIFICATE-----
MIIGBTCCA+2gAwIBAgIQB48KnQPfEZ5DTk/sG/AjWjANBgkqhkiG9w0BAQsFADCB
lDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1Jl
ZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjE+MDwGA1UEAxM1
TWljcm9zb2Z0IERldmVsb3BtZW50IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5
IDIwMTQwHhcNMTQwNTI4MTY0MzQ2WhcNMzkwNTI4MTY1MTQ4WjCBlDELMAkGA1UE
BhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAc
BgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjE+MDwGA1UEAxM1TWljcm9zb2Z0
IERldmVsb3BtZW50IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTQwggIi
MA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDCD39tSbs58E2UP+j7TcXrO+Eo
WrmJKkZ+pcMzJx2CiT/rM6GHaurogrnaw5130TXAy4M2cqZXGRK8FeLIPHuDYjQU
1au23jaLoVpxplGWpwYzsyIdFGJTwqWvmkDKvixIVJnnKpNop2kZC5lpO8GyrK6U
3F+rfgLK3jyndKaMEKDlrracNe+DixDllyq6kWuaakWV2dBUcY5lP8SKU8oeOEcK
6dBBhKXaHmYBZQTmUFt3NfW0LikyDMa/X2HuMiC3fDn5Efr/YF7+xmn0bx4d7R0G
52UemhEuY0QGXzFDFzPpoyaC1EuDEk/SoSYDJUjhOr2E9YrVtG4a6HEgDkVTAWet
4x5r6LLkq/31O466Z69ZhMxcddCdqlxyxCY2oqwyTGqx+DMXRNKnfXDu63CUmrzq
uhwQS2NbON3SJUUEsvCzWnwLCo4hQGQ3EU2WaUUz5JODnvmztRwrBXHqbcznSLa2
3oBQEMpJOLNZBXBOvZ6IAiJYZInrQNqxLS1qQIhdI8M+0PXVt5CKKFQ5YqLFxrG/
dM2GlflFa8zyB+qsXNM296J6tbRyUyoGPsM3lFhYsUpxu1zNnLKvEJrZQzY+UoUZ
50IokRGMjOe73+bIVQhzdfOWDYa30uUGssCKVKhhdyB9bNH+umjzRUqvEYTrhn0v
BPNU6iD/1ds9JQJwhwIDAQABo1EwTzALBgNVHQ8EBAMCAYYwDwYDVR0TAQH/BAUw
AwEB/zAdBgNVHQ4EFgQUhXAAn3dZHoysPJ93JigZzJrBjzIwEAYJKwYBBAGCNxUB
BAMCAQAwDQYJKoZIhvcNAQELBQADggIBAE8ldL0fYk9fD/dCItfR1lMEIy7F1dcH
K2t5O19tkO0TVdOC8fUCjz75liZ+DUIYdvxgVYJahr0RMzlpD87gsCvxXRnf2NL6
hqTMzazw0K6aiyskjwPBNQ0gs9/HQup3KS4KEvwLGkWN2TGEDY0CwKz60hK/Hmo0
PuqDAKNIdU5yZi2hpRKfN6hdSndZz9Y6/DDFpgmlv7EI4/ssn3bE+05hHW0j83Zp
hetJuw33PdCqBbzdPW6ARF7ZmmjsyYnH5hoY+GCg54z25lFvDuAluGP5+cILjDyc
svBCzb7D9f5JKVWcXoaW+6HtbSaG6Lggi1zG5y0xxarKfUt9oFmkHvtQcemvz9aq
DZnejpUmlzGl9H9t9GgVuOP3rdjv0Th1Al/9bU78tvwvRRupytEeev91GBU2wSDk
X0g6let75PX29P7JSyGiqeqKmSXL6ERAkNU5tGsjm1K8wMF+F2ZuZQv1dBWWqGbt
hWhUsiTodYhkRYmFPHpla5bg8lnqRyVmD2obDD/USuZLJhdHCf7U17jgzucvlK2A
i2dwzLd7zxsrudFbvbgDXLHwG0Es5lNVFudKDkEImTfiqddtDmpF5ezjiKn9tpvD
KCDOq8KTa1FlU7+gXnudJjSaUUyMpjjVhls8Ve5Q7AALyqzcyhCr3xib0qwMjQhF
Fa+FNTVa5Sa8
-----END CERTIFICATE-----
Above certificate is base-64 encoded CER file for the “Microsoft Development Root Certificate Authority 2014”.
Windows Server 2025 – preview build 26080
Last week on 13th of March Microsoft announced (RSS) new preview release of Windows Server 2025 (Windows Server Long-Term Servicing Channel (LTSC), build 26080). This preview build contains both the Desktop Experience and Server Core installation options for Datacenter and Standard editions, Annual Channel for Container Host and Azure Edition (for VM evaluation only):
To download evaluation (build 26080 will expire after September 15, 2024) version of new Windows Server 2025, go to Windows Insider Preview Downloads. To download preview Server versions, you need to be a member of the Windows Insider program. If you are not yet an insider, you can register for free here.
Besides English (US) version, you can also test server in few other languages:
Two of the most interesting changes in this new release are:
– Win32-OpenSSH server component is now installed by default,
– winget in Windows Server with Desktop Experience.
Starting in Windows Server 2025 the Win32-OpenSSH server side component (SSHD) will ship installed by default and if/when needed, it just needs to be enabled/disabled:
By default, when SSH is enabled, it will allow inbound connection on private networks (only) on the default TCP port 22. New local group “OpenSSH Users” can be used to allow remote connectivity for non-admin users.
Enable command that is executed in the background:
Get-Service -Name sshd | Set-Service -StartupType Automatic -PassThru | Start-Service
Disable command that is executed in the bckground:
Get-Service -Name sshd | Set-Service -StartupType Manual -PassThru | Stop-Service -Force


To customize default SSH config, you can edit file “C:\ProgramData\ssh\sshd_config”.
Some of the defaults:
AllowGroups administrators “openssh users”
HostKey PROGRAMDATA/ssh/ssh_host…
AuthorizedKeysFile .ssh/authorized_keys
Match Group administrators
AuthorizedKeysFile PROGRAMDATA/ssh/administrators_authorized_keys
Winget (Windows Package Manager) is command-line tool originally available on Windows 11 and modern versions of Windows 10. It allows admins and users to manage (install, uninstall, upgrade,…) locally installed applications. Winget is designed to help you quickly and easily discover and install custom software packages (by default from two sources: winget and msstore, with support for more).
Until you start managing applications with a solution like AppLocker, you might want to use GPO to disable winget.
If you want to test matching version of Windows Client, you can also download Windows 11 Insider Preview Build 26080:
Since Windows 11 Insider Preview Build 26052 you can natively run sudo on Windows 11, you just need to enable it:

Unlike winget, for this one I do hope it gets added to Windows Server at some point…
More info:
– Announcing Windows Server Preview Build 26080
– Introducing Sudo for Windows
Microsoft news in June 2019
So far June has been busy month for Microsoft. Few of the recent announcements I want you to know about:
– Microsoft Azure Bastion – private and fully managed RDP and SSH access to virtual machines (blog)
– AaronLocker performance and feature updates (blog)
– Microsoft Hyper-V Server 2019 available for download (ISO)
– Sysinternals updates
– Sysmon v10.01 – adds support for DNS query logging
– Autoruns for Windows v13.95 – adds support for user Shell folders redirections
– Windows To Go (WTG) – Feature Deprecation in Windows 10 1903
– PowerShell v7.0.0-preview.1 Release
– Azure Multi-Factor Authentication Server goes Cloud-Only – As of July 1, 2019, Microsoft will no longer offer MFA Server for new deployments.
– Microsoft Edge Insider Channels receives update on Canary channel – brings preview for Windows 7, Windows 8, Windows 8.1 and macOS (*)
– SCCM Client extension for Windows Admin Center (more info) (*)
– Windows Insider Lab Kit (Olympia v2) updated to version 5.7 (*)
– Windows and Office Deployment Lab Kit updated to version 1903 (*)
* added after initial blog post
NTK 2019 and other Microsoft-related news
From 21. until 23. of May 2019, Portorož (Slovenia) became my home for few days. The reason for this was NTK (NT konferenca) – Microsoft’s IT conference that brought together people from all over the place.
During the three days conference was going on, I had a privilege to present three sessions of my own. As always, I was pleasantly surprised by the number of people who came to my sessions, even though the session was in the middle of the lunch time or the last one for the day. Thank you all for showing up and asking questions.
My sessions at NTK 2019 were:
- Povečanje varnosti Windows klientov – ways to improve Windows security
- Vzdrževanje SCCM in WSUS okolja – SCCM and WSUS maintenance
- Brezplačna orodja za upravljanje Windows okolij – free tools to speedup Windows maintenance
Presentations and demo files can be downloaded from NTK web site or from my OneDrive:
- Povečanje varnosti Windows klientov.pptx, Day1-Demos.zip
- Vzdrževanje SCCM in WSUS okolja.pptx, Day2-Demos.txt
- Brezplačna orodja za upravljanje Windows okolij.pptx
For all the demos on day one and day two I used Start-Demo.ps1 PowerShell script. Thank you Jeffrey Snover and Joel “Jaykul” Bennett for the original script.
During one of my presentations there was one Windows Sandbox related question – data sharing between Host and Sandbox. At the time I wasn’t aware of Windows Sandbox – Config Files which I believe is exactly where the question was going. There is MappedFolders parameter, that gives us an option to map local drive into Sandbox on user’s Desktop. Mapped folder can be Read-Only or Read&Write. Example of Windows Sandbox Config file with few additional options: WindowsSandbox.wsb
While we were busy with NTK, Microsoft rolled out few new products, services and announcements:
- Windows 10 1903 (available on VL Service Center since 21st of May, on MSDN since 4th of April)
- Microsoft Security Compliance Toolkit 1.0 updated with final version of Windows 10 Version 1903 and Windows Server Version 1903 Security Baseline (more info)
- AaronLocker updated (info)
- Features in Configuration Manager technical preview version 1905 (Application groups, BitLocker management, Task sequence debugger,…)
- Microsoft Edge preview builds – Chromium-based (Beta, Dev and Canary)
- Application Guard for Chrome und Firefox
On-premises BitLocker management using System Center Configuration Manager
Beginning in June 2019, System Center Configuration Manager (SCCM) will release a product preview for BitLocker management capabilities, followed by general availability later in 2019.
Configuration Manager will support BitLocker for Windows 10 Pro, Windows 10 Enterprise, and Windows 10 Education editions. It will also support Windows 7, Windows 8, and Windows 8.1 during their respective support lifecycles.
SCCM will provide the following BitLocker management capabilities:
Provisioning
Our provisioning solution will ensure that BitLocker will be a seamless experience within the SCCM console while also retaining the breadth of MBAM.
Prepare Trusted Platform Module (TPM)
Admins can open the TPM management console for TPM versions 1.2 and 2.0. Additionally, SCCM will support TPM+PIN for log in. For those devices without a TPM, we also permit USBs to be used as authenticators on boot.
Setting BitLocker Configuration
All MBAM configuration specific values that you set will be available through the SCCM console, including: choose drive encryption and cipher strength, configure user exemption policy, fixed data drive encryption settings, and more.
Encryption
Encryption allows admins to determine the algorithms with which to encrypt the device, the disks that are targeted for encryption, and the baselines users must provide in order to gain access to the disks.
Policy enactment / remediation on device
Admins can force users to get compliant with new security policies before being able to access the device.
New user can set a pin / password on TPM & non-TPM devices
Admins can customize their organization’s security profile on a per device basis.
Auto unlock
Policies to specify whether to unlock only an OS drive, or all attached drives, when a user unlocks the OS drive.
Helpdesk portal with auditing
A helpdesk portal allows other personas in the organization outside of the SCCM admin to provide help with key recovery, including key rotation and other MBAM-related support cases that may arise.
Key rotation
Key rotation allows admins to use a single-use key for unlocking a BitLocker encrypted device. Once this key is used, a new key will be generated for the device and stored securely on-premises.
Compliance reporting
SCCM reporting will include all reports currently found on MBAM in the SCCM console. This includes key details like encryption status per volume, per device, the primary user of the device, compliance status, reasons for non-compliance, etc.
If you are familiar with Microsoft BitLocker Administration and Monitoring (MBAM), you probably noticed that above listed BitLocker-related SCCM improvements to come look a lot like MBAM features – and you would be correct to think that. The reason for that is in Microsoft’s announcement for the MBAM support – MBAM will end mainstream support on July 9, 2019 and will enter extended support until July 9, 2024.
Regardless of the MBAM situation, I sure am happy to see this new feature set is coming to SCCM.
More info at: Microsoft expands BitLocker management capabilities for the enterprise
AaronLocker – automate AppLocker configuration
AppLocker is application whitelisting security feature that became available in Windows 7 and Windows Server 2008 R2. With Windows 10 and Windows Server 2016 Microsoft decided to rebrand it to Windows Defender Application Control or WDAC for short. Other than rebranding it, AppLocker didn’t receive any major improvements. In most of the management tools you will still find it under AppLocker name.
If you want to learn more about it, I would recommend you to check out official documentation.
If you or your company is using Windows Enterprise or Education client operating system, then you should look at setting up AppLocker. The implementation itself doesn’t take much time but it can drastically improve overall security of Windows environment. In Windows 10 and Windows Server 2016 AppLocker represents one part of multi-layer defense strategy.
To ease the implementation, Aaron Margosis put together set of PowerShell scripts including detailed documentation called AaronLocker. What AaronLocker helps you do is automate most of the tasks needed to implement and maintain AppLocker.
Few of the nice to have features are:
– Selective scan of any folder and subfolders with rule merge
– Additional rules for domain-joined PCs
– Find user writable paths and set exclusions
– Exclude sensitive build-in Windows programs, that are rarely used by non-admins
– Policy report in Excel
– Audit and Enforce policy
– Audit/Enforce summary reporting from AppLocker Logs in Event Viewer
– Reporting supports forwarded events with Event Forwarding (How-to in the documentation)
– Detailed documentation including how to implement Pilot / Broad / Production phases
You can learn more about AaronLocker from the documentation available on the GitHub portal. If you prefer or like video content, you can also check two YouTube videos, first one introducing the solution and second one quick start.
SloWUG – 2019.02 – Pohitrimo nadzor Windows okolja s SCCM
On 13th of February I was presenting at Slovenian Windows Users Group (SloWUG) in Ljubljana. We looked at different SCCM features, some fully released, some in preview in latest stable build (1810) and some in preview in preview builds. Focus of the presentation was on the features administrators can use, to decrease time of their daily work and at the same time improve existing procedures.
Attached to this post you can find link to my presentation.
After short discussion with attendees, I plan to do another SCCM-related presentation, this time focusing on SCCM maintenance and WSUS.
Windows Server 2016 – Where to start?
New version of Windows Server is by now available to all of us.
If you haven’t had a chance to look into it, here are few starting points for the journey ahead:
- Windows Server 2016 Feature Comparison Guide (PDF)
- Introducing Windows Server 2016 (PDF)
- Microsoft Ignite On-Demand Videos – Windows Server 2016
If you haven’t yet downloaded your copy, you can grab one here:
After you get through all previous content, you might also be interested in:
- Nano Server Image Builder (download)
- MSMG Toolkit (automate Windows Image management tasks like Servicing, Customization, Add or Remove Features and Components, Enable or Disable Features)
- Security baseline for Windows 10 v1607 (“Anniversary edition”) and Windows Server 2016
- AD FS Rapid Restore Tool
SCCM 2012 R2 With BitLocker Network Unlock
I’ve read and followed MS documentation available at:
– BitLocker: How to enable Network Unlock
– Bitlocker: Network Unlock (PFE Blog post)
- Client/Server configuration:
- Clients: Windows 8.1 and up on isolated VLAN
- SCCM Servers: 2012 R2 SP1
- SCCM distribution point: dedicated server for network unlock and client deployment
- change to certificate template used for network unlock: Certification Authority and Certificate recipient fields are Windows Server 2012 R2 and Windows 8.1 respectively
After some initial testing I’ve successfuly deployed this configuration at one of our customer’s sites.
Not sure if it is fully supported from MS side but I didn’t do any “funny” customization to get it working – based on this I would guess it should be supported.
Second link is really useful for understanding how the whole thing works – it even has few screenshots of network trace (good reference for troubleshooting).
Good to know:
– Network unlock by itself doesn’t do PXE boot – unlock happens before that with special DHCP packet (provided, that LAN boot is not first BOOT option – which it shouldn’t be). Check second link for more info.
– This change to BitLocker OS drive unlock process will add few seconds to boot process. Why? Before Windows can successfully start and unlock drive with certificate, boot manager has to get valid IP DHCP address (or not if timeout happens). Only after this happens BootRequest packet is send to WDS server which replies with BootReply. How big can this delay be probably depends on usual network-related configuration.
Where to start your journey when your goal is multi-boot USB
Not so often anymore, but still sometimes I find myself in situation when I have to analyze and possibly repair broken Windows system. When that happens, it is good to have few tools at hand. Because you never know what went wrong in advance, it is good to be prepared for all occasions. I usually need only one USB drive – my 32GB multi-boot USB drive (you can also go with less).
On my USB, there are quite few tools; some of them might come in handy even to you some day. Just to kick-start your journey I will give you few pointers:
You need bootable USB and something to boot. I prefer:
Windows 7 USB/DVD tool
– Free
– Good for Windows-only multi-boot
– Wizard driven “ISO to USB/DVD” converter
– Can create bootable USB from any WIM based image, like:
– Windows Vista & Windows Server 2008
– Windows 7 & Windows Server 2008 R2
– Windows Defender Offline
– Microsoft Diagnostics and Recovery Toolset
– Windows PE – you can get it in Windows AIK
– Windows RE – Create a Windows RE Recovery Media
Windows Defender Offline
– Free
– Dedicated to finding and removing malicious and potentially unwanted programs
– Based on Windows PE
– Wizard driven USB/DVD creator
Microsoft Diagnostics and Recovery Toolset
– Free for Microsoft SA customers, available to Volume Licensing customers, Microsoft Development Network subscribers, and Microsoft TechNet subscribers
– Packed with tools like Locksmith, Crash Analyzer, File Restore, Disk Wipe and Standalone System Sweeper
– Based on Windows PE
– Wizard driven USB/DVD creator
Universal USB Installer
– Free
– Great for true multi-boot
– Can combine multiple Windows based and non-Windows based images onto one media
– Supports Windows XP and newer
– Supports 90+ Linux distributions (don’t forget to check out KON-BOOT*)
– Wizard driven USB/DVD creator
When creating bootable USB all the applications require USB format (wipe and FAT32 created).
If you also like to have updated Sysinternals tools with you, don’t forget to check out SysInternalsUpdater.
*Great tool for true bypassing of local Windows Logon passwords.



